Which Best Describes An Insider Threat Someone Who Uses: Best Picks & Buying Guide
Alright, gather ‘round, folks! Picture this: you’re at your favorite cozy café, the aroma of freshly brewed coffee is doing its magic, and you’re about to hear a tale that’s as juicy as a gossip magazine, but with a sprinkle of actual, useful information. We’re diving into the mysterious world of… well, let’s call them “insider threats.” Now, before you start picturing someone in a trench coat whispering secrets in the breakroom, let me tell you, it’s often a lot more… mundane. And sometimes, way funnier. Or scarier. Or both!
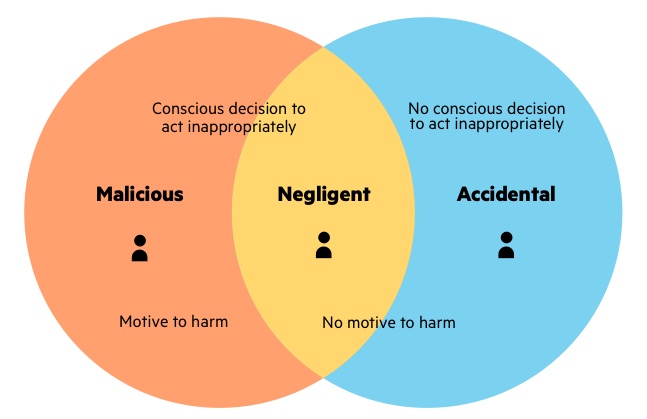
So, what exactly is an “insider threat”? Is it your grandma trying to “fix” your laptop by repeatedly hitting it with a wooden spoon? (Though, bless her heart, she’s probably just trying to help!). Is it that overly ambitious colleague who’s secretly trying to steal your brilliant ideas for the office potluck? (Again, bless their competitive spirit, but maybe they just really like your guacamole recipe). Nope, in the slightly more formal, definitely less delicious world of cybersecurity and business, an insider threat is basically someone who has authorized access to an organization’s systems or data, but then uses that access in a way that causes harm.
Think of it like this: you’ve given your best friend the spare key to your apartment. They’re totally trustworthy, right? They’re not going to, like, steal your vintage Star Wars action figures. But what if, in a moment of extreme snack-craving laziness, they decide to order a ridiculous amount of pizza and have it delivered to your place without asking? That’s a minor inconvenience, but it’s still an “abuse of access,” wouldn’t you say? Now, scale that up to a multi-billion dollar corporation and sensitive data, and suddenly that pizza delivery looks like a data breach that makes the evening news. Oopsie!
The “Oops, My Bad” Insider
Let’s talk about the most common type of insider threat, the one that’ll make you sigh and shake your head rather than call in the secret service: the “Oops, My Bad” Insider. This is your everyday employee who, through sheer carelessness or a series of unfortunate events, ends up compromising something important. They’re not malicious; they’re just… human. And humans, my friends, are prone to making mistakes. Like leaving their company laptop unlocked in a coffee shop while they pop out to Instagram their latte art. Or clicking on a phishing email that promises them a free unicorn. (Spoiler alert: unicorns are notoriously hard to deliver via email.)
These folks are the reason we have those mandatory cybersecurity training sessions that feel like they were designed by a robot with a sugar crash. They’re the reason IT departments have to implement more complex password policies than a secret society initiation. And bless their cotton socks, they’re usually the first ones to apologize profusely when things go wrong. "Oh, you mean I shouldn't have downloaded that suspiciously free antivirus software from a pop-up ad that looked like it was designed in the early 2000s?" Cue dramatic sigh.

A surprising fact? Many insider threats aren't even intentional! Studies suggest that a significant chunk of data leaks and security incidents are caused by accidental disclosures or negligence, not by shadowy figures plotting corporate espionage. So, that colleague who’s always blasting loud music and accidentally forwarding emails to the entire company? They might just be your biggest security risk, without ever meaning to be.
The “I’m Just Trying to Make a Quick Buck” Insider
Then we have the slightly more unsettling category: the “I’m Just Trying to Make a Quick Buck” Insider. These are the individuals who, for whatever reason – maybe they’re unhappy with their pay, or they’ve got a gambling problem, or they just discovered a black market for company spreadsheets – decide to deliberately misuse their access for personal gain. This can range from a disgruntled employee selling a customer list to a competitor, to someone stealing intellectual property to start their own rival business. Ouch.
This is where things get a bit more… detective-y. These are the folks who might be exhibiting unusual behavior, like working late hours without explanation, accessing files they have no business with, or suddenly becoming very interested in the company’s financial projections. It’s like that one friend who always “borrows” your favorite pen and never returns it, but instead of a pen, it’s the secret formula for your company’s best-selling product. Not cool, man. Not cool.

These threats are harder to spot because they’re often more clandestine. They’re not going to announce their intentions. They’re the quiet ones, the ones you might underestimate, who are actually running a side hustle selling your company’s internal memos on the dark web. It’s like finding out your friendly neighborhood librarian is secretly a master spy. Who knew?
The “Revenge of the Underappreciated” Insider
And finally, we have the wonderfully dramatic, the tragically theatrical: the “Revenge of the Underappreciated” Insider. This is the employee who feels wronged, overlooked, or downright betrayed by their organization. Maybe they were passed over for a promotion, maybe they feel their ideas have been stolen, or maybe they just had a really, really bad performance review. Whatever the trigger, they decide to inflict a little pain back on the company that (in their eyes) has wronged them.

This can manifest in various ways, from deleting critical files out of spite, to sabotaging systems, or leaking damaging information to the press. It’s the corporate equivalent of a toddler throwing a tantrum, but with potentially millions of dollars in damages. Imagine if that colleague who always complains about Brenda from accounting decided to "accidentally" delete all of Brenda's spreadsheets just before the quarterly report. Chaos!
These are the insider threats that often come with a side of emotional turmoil. The individual might feel justified in their actions, believing they are leveling the playing field or seeking justice. It's a stark reminder that employee morale and fair treatment are not just "nice-to-haves," but crucial components of a secure organization. Because a truly unhappy employee? They can be more dangerous than a hacker with a supercomputer and a vendetta.
So, Who’s Using What? Best Picks & Buying Guide (Sort Of!)
Now, you might be wondering, “Okay, this is all fascinating, but what does this have to do with ‘Best Picks & Buying Guides’?” Well, it’s all about understanding the motivation behind the threat. When we talk about “who is using what” in the context of insider threats, we’re not talking about choosing the best brand of artisanal cheese. We’re talking about how individuals are leveraging their access.

Are they using their access to steal data for personal gain? That’s your “Quick Buck” insider. Are they using their access carelessly, clicking on dodgy links? That’s your “Oops, My Bad” insider. Are they using their access to inflict maximum damage out of pure frustration? That’s your “Revenge” insider.
The “buying guide” aspect? Well, it’s a bit tongue-in-cheek. In a real-world scenario, a company looking to prevent insider threats would be “buying” solutions like robust access controls, employee monitoring software (with ethical considerations, of course!), regular security training, and strong HR policies that address employee grievances. They’re essentially “buying” peace of mind by investing in proactive security measures.
Ultimately, understanding the different types of insider threats helps organizations build better defenses. It’s about recognizing that the biggest security risks might not be external hackers in hoodies, but the person sitting right next to you, who might be having a very bad day, or just a really, really strong craving for that unicorn. And that, my friends, is the most surprising fact of all. Now, who wants another coffee?
